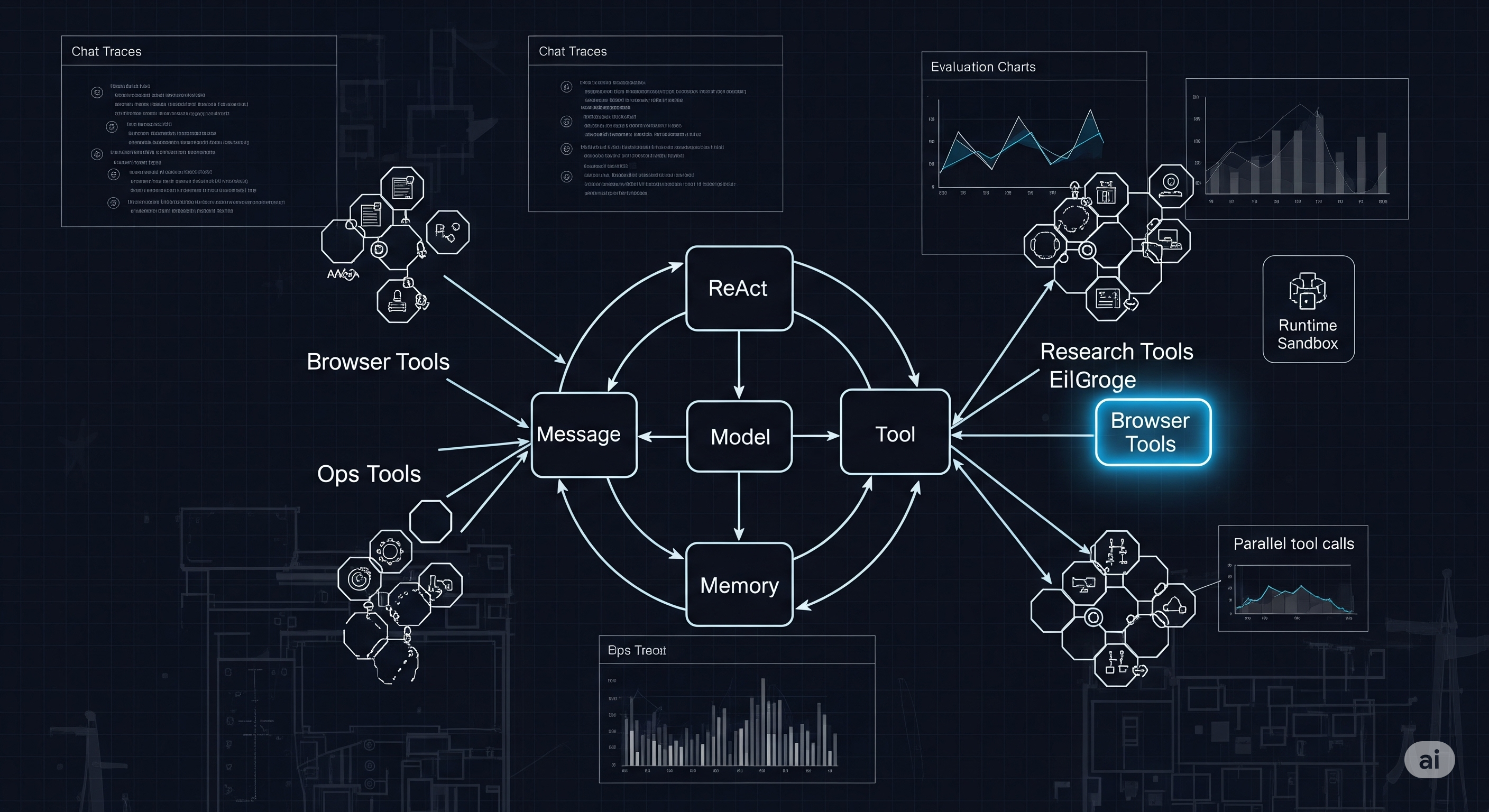
Traffic, but Make It Agentic: When Simulators Learn to Think
Opening — Why this matters now Traffic simulation has always promised more than it delivers. City planners, transport researchers, and policymakers are told that with the right simulator, congestion can be eased, emissions reduced, and infrastructure decisions made rationally. In practice, most simulators demand deep domain expertise, rigid workflows, and a tolerance for configuration pain that few real-world users possess. ...