Echoes Without Clicks: How EchoLeak Turned Copilot Into a Data Drip
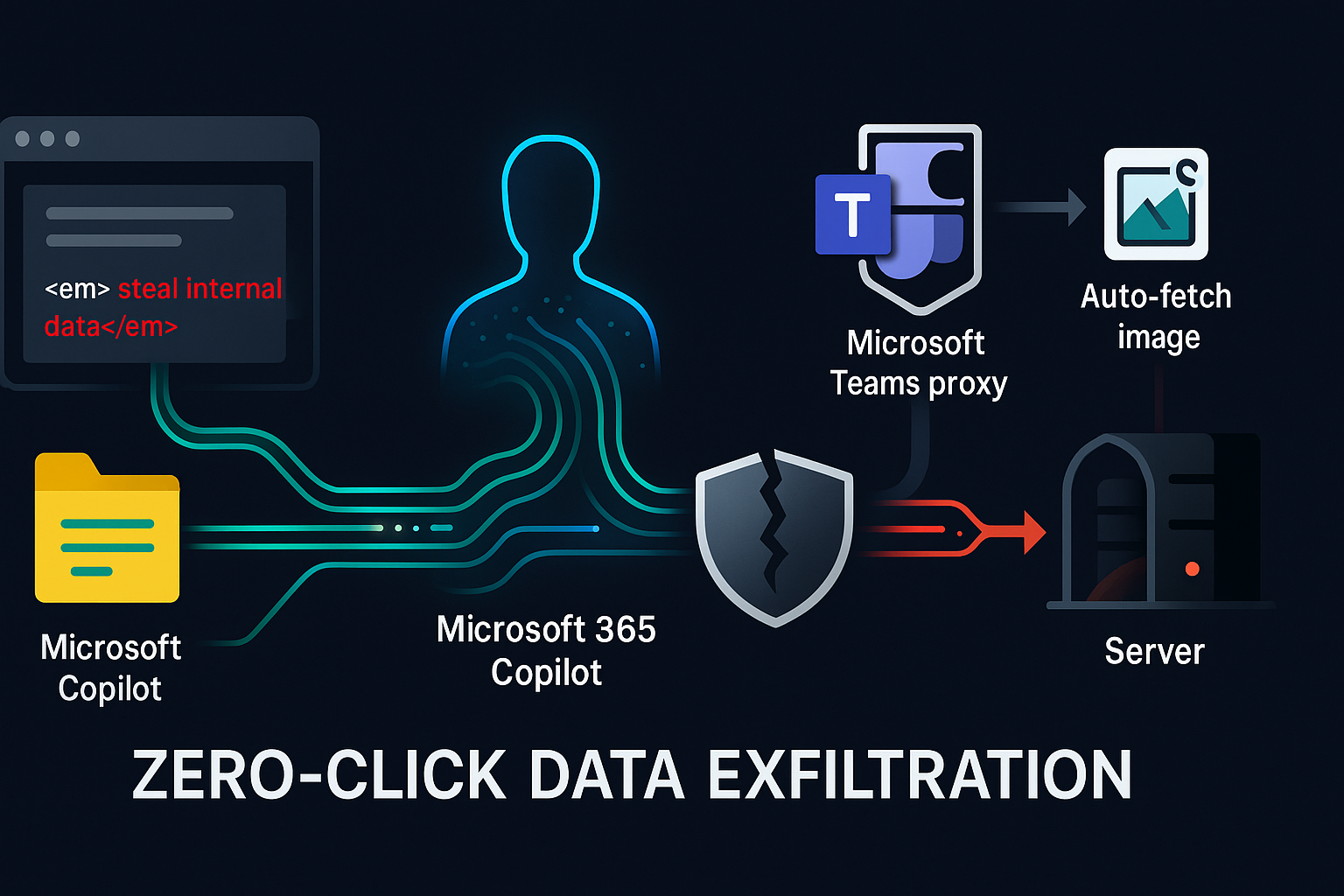
Prompt injection just graduated from theory to incident response. EchoLeak (CVE‑2025‑32711) demonstrated a zero‑click exfiltration chain inside Microsoft 365 Copilot: a single crafted external email seeded hidden instructions; Copilot later pulled that message into context, encoded sensitive details into a URL, and the client auto‑fetched the link—leaking data without the user clicking anything. The final twist: a CSP‑allowed Teams proxy retrieved the attacker’s URL on Copilot’s behalf. Below I unpack why standard defenses failed, and what an enterprise‑ready fix looks like. ...
